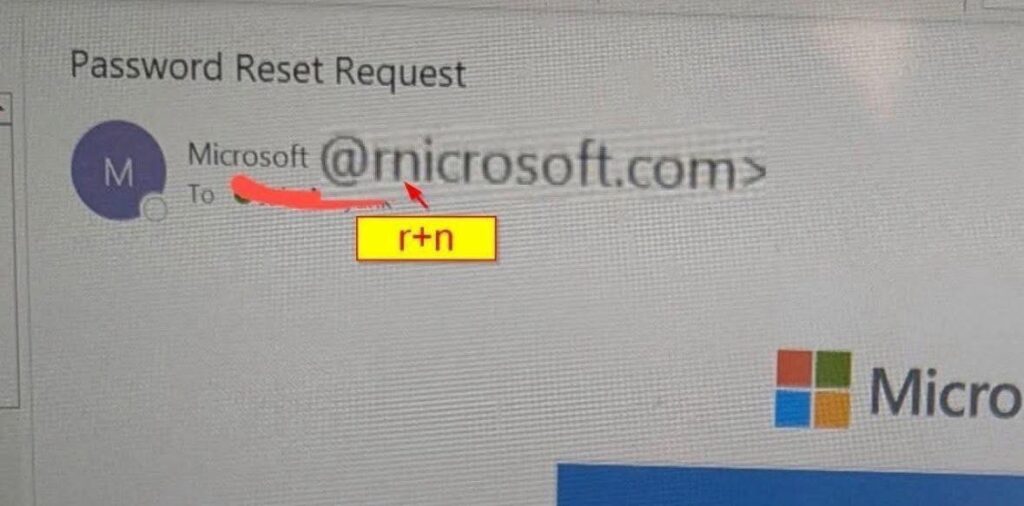
We’ve recently identified a dramatic increase in phishing attempts targeting businesses in the Cairns region and in particular their Microsoft 365 accounts. These attacks involve fraudulent emails designed to steal login credentials or trick you into clicking malicious links entering your username and password and authorising with a 2 Factor code, and then the session token is stolen and used elsewhere without your knowledge. We have attached some example email screenshots to watch out for, that we are actively detecting. Most attacks are coming in the form of SharePoint Document sharing links and View Document links within emails.
To protect your accounts and data, we urge you to stay diligent and follow these simple steps to spot and avoid phishing emails:
How to Identify Phishing Emails:
- Check the Sender’s Email Address: Look closely at the sender’s email. Phishing emails often use fake addresses that mimic legitimate ones (e.g., “support@micros0ft.com” instead of “support@microsoft.com”).
- Verify Links Before Clicking: Hover over links (don’t click) to see the actual URL. If it doesn’t match the expected website (e.g., login.microsoft.com), do not click.
- Watch for Urgent or Suspicious Requests: Be cautious of emails demanding immediate action, asking for passwords, or requesting sensitive information.
- Look for Spelling/Grammar Errors: Phishing emails may contain typos or unusual phrasing.
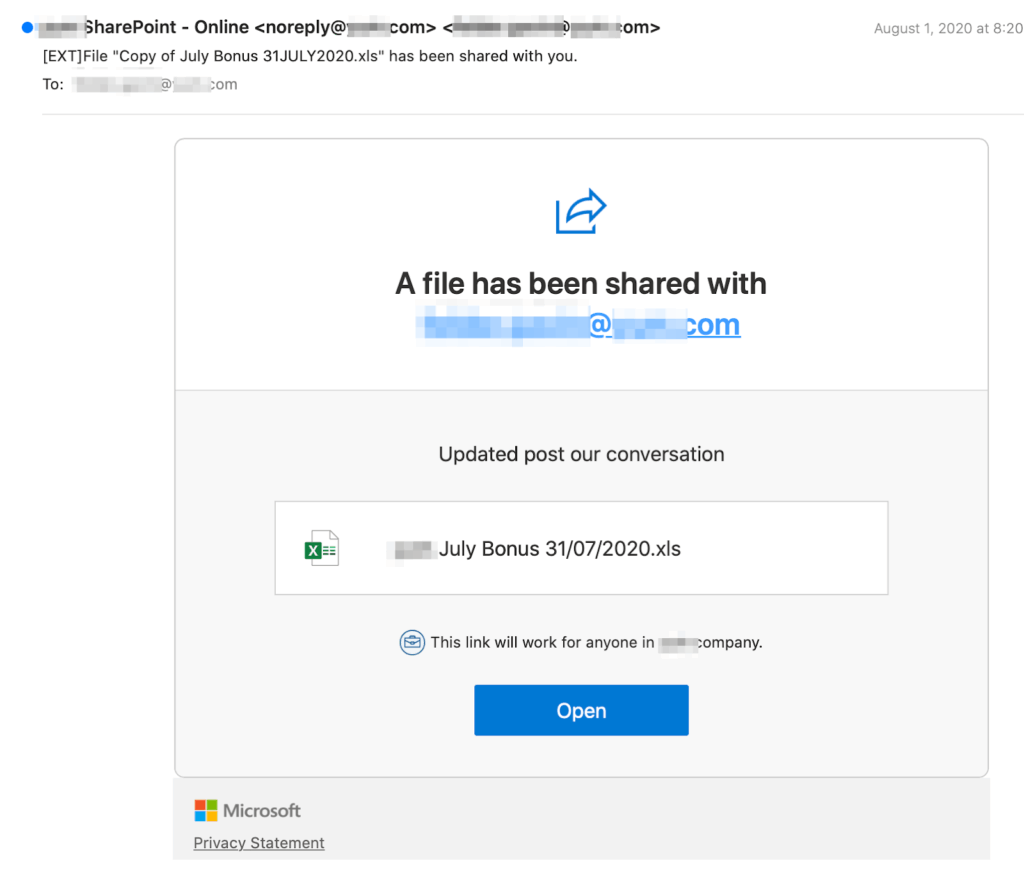
Example screenshot of a typical phishing scam requesting you to click on a link and inout your details, which they then steal.
What to Do:
- Do Not Click Suspicious Links or Attachments: If an email seems off, do not interact with it. Forward it to your IT contact at Realised Technologies for review.
- Manually Type URLs: For Microsoft 365, always type “login.microsoft.com” directly into your browser to log in safely.
- Contact Us Immediately: If you suspect you’ve clicked a phishing link or entered credentials, reach out to us at Realised Technologies on 0740514200) right away.
- Notify Your Contacts of Potential Compromise: If you suspect your account was compromised, let your contacts know to ignore any suspicious emails from you during the affected period.
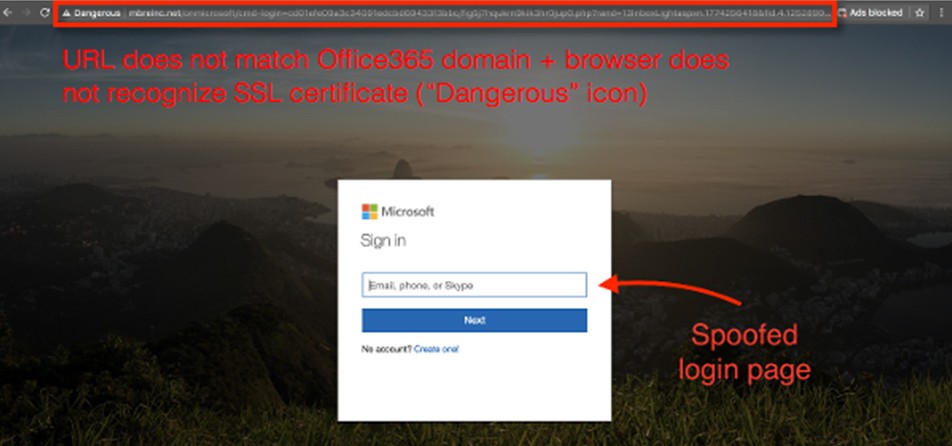
Example phishing login page: Do not sign into M365 Login page from links within an email. Even though this page looks legitimate, it is made that way to trick you into giving your password.
Our Actions to Protect You:
- We’re actively enhancing security for your accounts.
- Reviewing accounts for potential vulnerabilities and areas for improvement to your security posture.
- Setting up Security awareness training sessions to help educate you and your team of the ongoing Cyber Security concerns and best practices.
Stay Alert, Stay Diligent